Every year people anxiously wait for that shiny new phone, tablet, laptop or car and in most cases they end up being disappointed with a new expensive product that are not visually pleasing or provides very few advantages over the one they already have. (Pixel 4 wink wink)
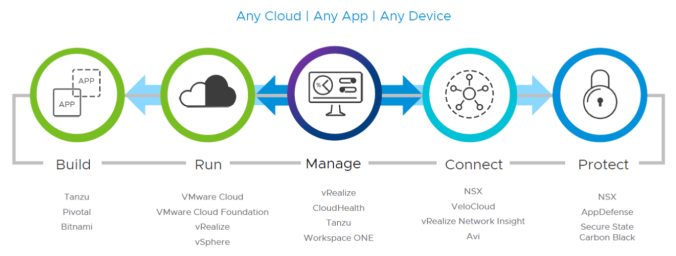
Well every year some of us get just as excited about software releases, and in most cases we experience the same ups and downs with new releases. But lately VMware with all their amazing strategic acquisitions, has been hitting it out of the park, and this year is no different and in my opinion a game changer with VMware expanding their portfolio to accelerate their strategy for any cloud, any app, any device as well as making Kubernetes available for enterprise adoption in vSphere, Public clouds an edge locations.
The IT industry is changing at a fast pace and so has the definition of an application. Apps used to be some monolith that consisted of a VM for the app and maybe another VM for the database and VMware provides a mature platform for these need, however now we are starting to see distributed systems where parts your application might be running in a VM, other parts running in containers that leverage Kubernetes as its control plane, and even consuming capabilities from other micro services like databases and serverless functions.

These modern applications create challenges for Developers, Line-of-business leaders, as well as creates complexities for the VI admin around provisioning, logging, monitoring, troubleshooting, backup/restore, networking and security. Not just on-prem, but in the cloud as well. VMware is looking to provide value across 3 different pillars.

These will be delivered through vSphere 7 capabilities as well as what VMware is referring to as “VMware with Kubernetes”.
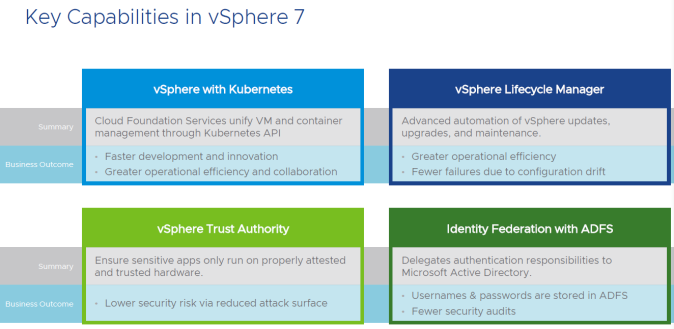
Let’s first do a deep dive into the non-Kubernetes side and of course where everything always starts, our beloved vSphere:
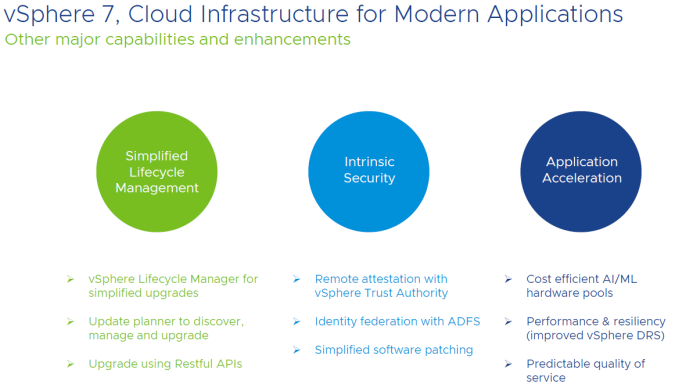
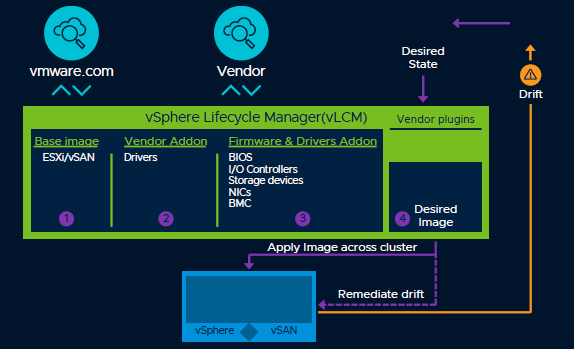
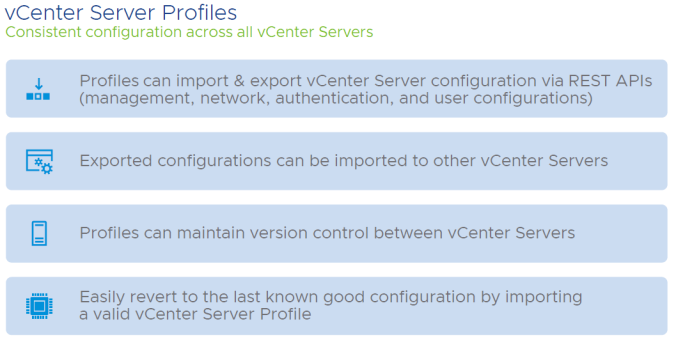
The primary focus in vSphere 7 is all about simplified Lifecycle Management, enhancing all the intrinsic security capabilities and the application accelerations deliveries capabilities. The capabilities and enhances that we will be discussing will be available with Enterprise Plus.

Since we have so much to cover, I have broken up the detailed review of each products new features and enhancements into different blog posts:
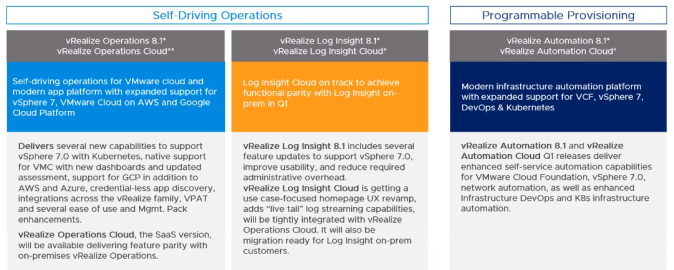
vRealize Management 8.1 (vROPS, vRLI, vRA): What’s new
VMware Cloud Foundation 4: What’s new
The announcements above are great, but the star of the show is VMware’s entry into the container world with worthy products that will help customers navigate with ease around the complexities of Kubernetes. You can read about it in more detail on my blog post below.
VMware new product announcements: vSphere with Kubernetes (Project Pacific) & Tanzu App Portfolio
(All images on this page courtesy VMware)